-
Public cloud isn’t risk-free
While public cloud offers several infrastructural benefits, organizations must reckon with the intricacies of the shared responsibility model.
-
Cyberattacks have eroded confidence in cloud security
The study notes a massive rise in cyberattacks targeting public cloud environments, making organizations hesitant to shift their workloads.
-
Key insights from CDW Canada experts
Our cybersecurity experts share insights, advice and strategies that can help organizations improve their public cloud security posture in conjugation with the study.
June 13, 2024
Is Public Cloud Security Still a Gray Area? CDW Experts Weigh In
CDW's 2024 Canadian Cybersecurity Study showed a growing concern around public cloud security. In this blog, our security experts scrutinize these findings and offer essential advice for organizations leveraging the public cloud.

The ubiquity of the public cloud in Canada has also led to a rise in cyberthreats. Our 2024 Canadian Cybersecurity Study found that public cloud had the highest share of IT components impacted by a cyberattack, jumping from 43.5 percent in 2022 to 56.7 percent in 2024.
These incidents have made organizations wary of migrating their workloads to public cloud. This year’s study found that one in three Canadian organizations believe they’ve been short-changed on the security in cloud promise.
Consequently, business leaders and IT decision-makers have tough technology concerns in front of them: How can they realize cloud benefits without compromising security, and is public cloud really unsafe?
CDW Canada’s cybersecurity and cloud leaders don’t think so. In this blog, we explore the findings of our Canadian Cybersecurity Study and offer expert advice from our leaders to help demystify the gray area surrounding security in public cloud.
Understanding the current landscape
Public cloud isn’t risk-free
Public cloud offerings can provide several benefits, such as running IT infrastructure virtually and scaling up capacity without using any servers on-premises. Furthermore, the extensive security measures taken by public cloud providers can help improve an organization’s security posture and facilitate business continuity.
However, as remarked by Ried Nilson, Principal Field Solution Architect at CDW Canada, these benefits come with some considerations. “While public cloud is great for accelerating innovation, reducing costs by eliminating hardware and providing scalability, it can also introduce additional risk to the organization,” he said.
Cloud providers alone can't guarantee the security of cloud-based workloads – they can only ensure that the underlying cloud platform stays resilient. The customer must be responsible for the security of the applications and data hosted in the cloud.
Cyberattacks have eroded confidence in cloud security
To support fast-growing digital initiatives, many organizations have become increasingly reliant on cloud services, which in turn increased their attack surface. Cyberattackers were quick to realize that any gaps in implementing public cloud security controls could be readily exploited.
These attackers devised sophisticated attack methods to target public cloud environments, such as:
- Social engineering tactics to steal cloud login credentials from vulnerable users
- Exploiting cloud-specific vulnerabilities or misconfigurations to gain unauthorized access
- Targeting cloud storage systems with ransomware attacks to inflict greater damage
- Using cloud’s massive compute power as a launchpad for cryptojacking
According to our study, many organizations have seen their confidence in public cloud systems affected as a result. It was observed that 34.8 percent of organizations believe that their cloud migration has underdelivered on security expectations.
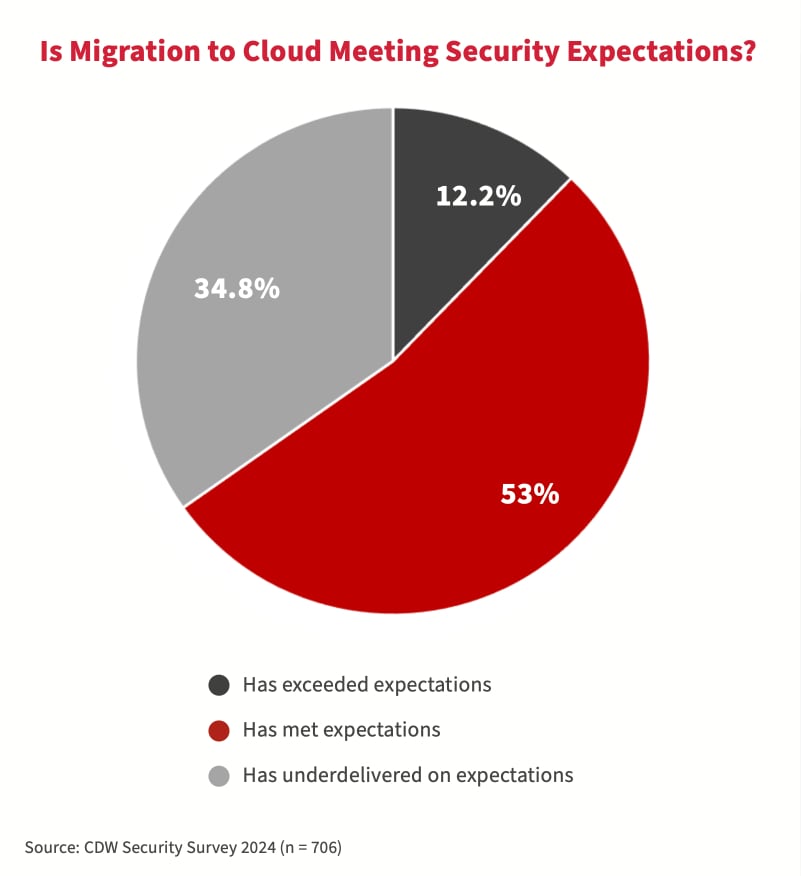
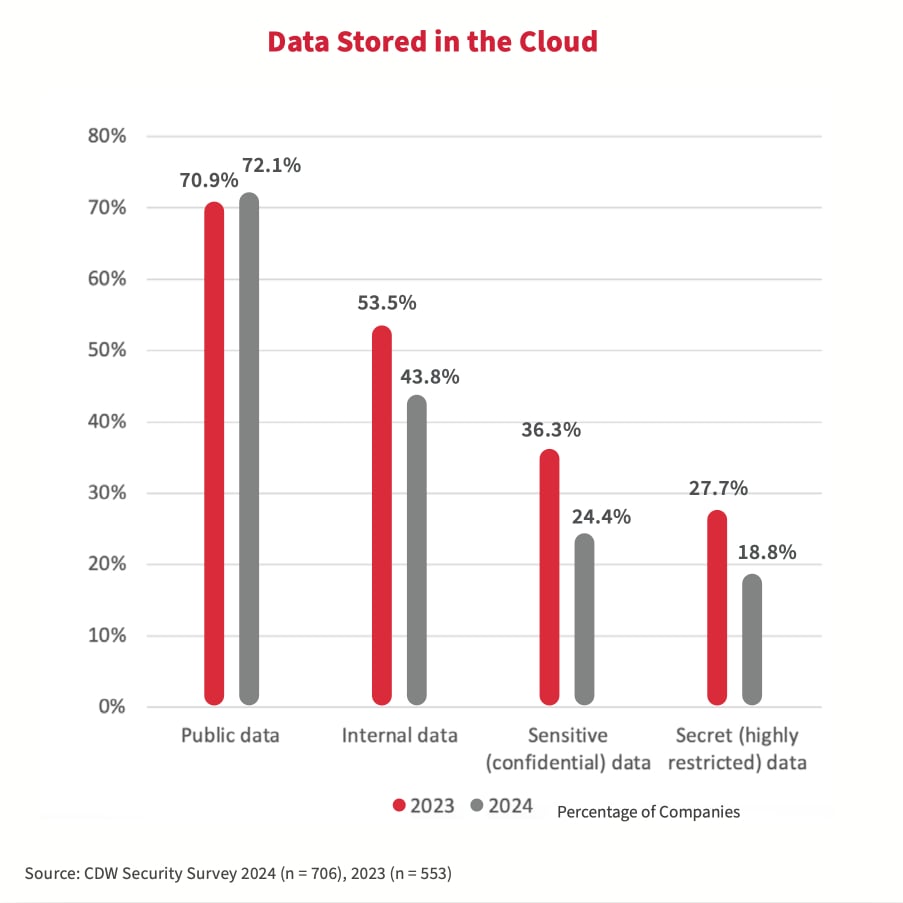
At the same time, fewer organizations stored their confidential and secret data in public cloud compared with the 2023 study. The top reason cited by 74 percent of respondents in the 2024 study was concerns about security.
4 key cloud security insights from CDW Canada experts
1. Focus on identity and data protection
Nilson suggests the two focus areas that can help cloud customers strengthen their end of the cloud’s shared responsibility model are identity management and data protection.
Identity management refers to the user accounts and associated privileges with which users access cloud services. As per Nilson, the following practices can help organizations keep risks in check:
- Implement multifactor authentication: At a minimum organizations should configure two-factor authentication to ensure that an attacker can’t easily use a compromised account to access the services.
- Leverage cloud-native anomaly detection: Configure built-in features provided by identity service providers to automatically identify potentially compromised accounts and enforce remediation actions such as forcing a password reset.
- Account lifecycle management: Processes and procedures related to account lifecycle are also important; permissions associated with accounts should be updated every time the user changes roles to ensure that the account isn’t overprovisioned with permissions.
“Cloud services may seem to have infinite redundancy and to be resilient to failures, but data protection does need to be taken into account when using cloud services,” Nilson says.
“Misconfiguration or mistakes can lose data or a threat actor may encrypt or delete data stored on a cloud service as part of an attack. Organizations must perform a gap analysis between what is provided from the cloud service provider and their key requirements.”
This can help address security gaps upfront and shrink the attack surface area. Also, early risk analysis goes a long way in ensuring the architecture of cloud services is secure by design.
2. Zero trust and DevOps as fundamentals for cloud benefits
The 2024 Canadian Cybersecurity Study pointed out that more organizations have adopted zero-trust security and associated technologies. 57.8 percent of organizations believe that zero trust benefits them in accelerating digital transformation across cloud, IoT, mobility and more.
Roshan Abraham, Principal - CISO Advisory Services, CDW Canada, emphasized that the success of public cloud adoption is tightly linked to the adoption of zero trust and DevOps principles.
“The story of public cloud is really a story of zero trust and DevOps. If you're able to use those two, you are well on your way towards those as baked into your operating posture and you're probably seeing the benefits of the cloud,” he said.
How can zero trust and DevOps help?
Zero trust enhances security by ensuring that no entity, whether inside or outside the network, is trusted by default. Instead, every access request is verified, making it harder for attackers to exploit vulnerabilities. This granular approach to security is essential in a cloud environment where traditional perimeter defences are less effective.
DevOps principles improve the efficiency of cloud operations by fostering a culture of collaboration between development and operations teams. This leads to faster development cycles, more reliable releases and quicker responses to incidents.
Abraham noted that organizations embracing DevOps principles are “likely having a better success rate in finding the benefits of the cloud.” This collaborative approach is vital in the dynamic and scalable nature of cloud environments.
3. Employ vendor management best practices to counter risk
Before selecting a cloud services vendor, organizations must diligently check if their architectural requirements will be met. The study reported that 46 percent of organizations attribute their concerns about storing data in public cloud to gaps in cloud vendor compliance management, while 58.2 percent of respondents believe it’s because of concerns over maintaining internal compliance.
To mitigate this problem, Daniel Pinsky, CSO & Head of Security Governance and Compliance, CDW Canada, offered a three-step approach. “We can delegate control responsibility but not accountability,” he said.
1. Vetting your cloud service provider
When choosing a cloud service provider (CSP), it matters that the provider can meet your compliance needs. Remember that the cloud is essentially your data residing on external servers. Investigate your CSP’s track record – reliability and trustworthiness are paramount. Understand the types of data they’ll handle (business, PII, PHI, credit card info). Ask about subcontractors and ensure compliance with industry frameworks (ISO, NIST, PCI, SOC2).
2. Ongoing accountability and maintenance
Once you’re in a CSP relationship, you can continue to maintain compliance with the help of the following measures:
- Scheduled meetings: Regularly discuss security performance with your CSP.
- SLAs and metrics: Set clear expectations and track relevant metrics.
- Annual audits: Mandate annual audit reports for transparency.
3. Exiting gracefully: protecting your interests
When parting ways with a CSP, it’s critical to have an exit strategy that highlights how the associations will be wound down. Some of the key aspects of the strategy are as follows.
- Deprovisioning: Revoke access rights promptly.
- Intellectual property: Clarify ownership of any intellectual property developed during engagement.
- Information portability: Plan for data migration.
- Confidentiality: Maintain it even during the transition.
By following these steps, organizations can navigate cloud security effectively and ensure that vendor compliance remains intact.
4. Go beyond point solutions by incorporating security in your cloud design
Despite increased investments in cloud security, the 2024 study data does not show a significant reduction in cloud security incidents compared with the previous study. Why? Investing in point solutions might not reduce security incidents because it addresses specific use cases rather than the broader cloud architecture.
Nyron Samaroo, Principal Field Solution Architect, CDW Canada, advised tackling security as a part of the cloud design process. “Have a design of what your cloud environment is going to look like and then that cloud environment is built against that design. The design should account for all your security controls.”
How cloud design affects security
Cloud design refers to the planning and structuring of a cloud environment before its implementation. This involves creating a detailed architecture that takes the entire cloud environment into consideration and not just one aspect.
Proper cloud design requires a strong focus on security from the outset. This proactive approach helps mitigate risks and ensures that security is not an afterthought but an integral part of the cloud infrastructure.
For example, CSPM and CASB for access control, firewalls for cloud and VPN for cloud all support a single use case, thereby leaving gaps in security. These solutions do not account for the dynamic and complex nature of cloud environments.
Even if there are higher potential costs for initial design, Samaroo pointed out that this can save money in the long run by preventing delays and security incidents: “Having a cloud design beforehand saves organizations in the long run, by reducing delays and decisions that come out of that.”
Conclusion
The evolving threat landscape may stifle organizations from fully realizing their public cloud investments. But with a foresight of risks and awareness of cloud-native best practices, their digital initiatives can become resilient to threats.
In addition to security in public cloud, our 2024 Canadian Cybersecurity Study touches upon several other security insights that are of interest for IT leaders. Use the following hyperlink to unlock full insights.
